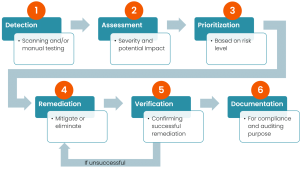
Our Vulnerability Management and Assessment services provide a structured, comprehensive approach to identifying, evaluating, and mitigating vulnerabilities across your organization’s systems, networks, and applications. With a focus on proactive security, our services include the following key components:
Vulnerability scanning is an inspection of the potential points of exploit on a computer or network to identify security holes. A vulnerability scan detects and classifies system weaknesses in computers, networks and ...
we perform a thorough verification process before deploying any patches or updates. This includes checking the file hashes to ensure the integrity and authenticity of the downloaded files and checksum validations. Deployment is both manual and automated.
We support some of the common cyber security compliance standards scans that help to form a strong basis for a good cybersecurity strategy. Scanning for Compliance standards like PCI DSS, HIPAA, GDPR IV, NIST 800-53, NIST 800-171, CIS, CIS 8.0, ISO 27002, and Essential Eight is supported with ...
All assets, firewalls and other assets including software inventory. Assets are added and Monitors are added automatically based on the type of asset added, problems, solutions, external assets, depreciated assets and individual asset health report.
We scan for Personally identifiable information (PII) is information that, when used alone or with other relevant data, can identify an individual.
View all certificates found during external scanning jobs across companies with key information about the certificates. This includes Company Name, Asset Name, IP, Port, Issuer, Not Valid After, Not Valid Before, SSL Expired Status...